Explain the Different Types of Targeted Malicious Codes in Detail
A worm is a malicious software which similar to that of a computer virus is a self-replicating program however in the case of worms it automatically executes itself. Different Types of Malware Running into the word that starts with mal is a literal sign that something is bad.

Virus And Malicious Code Chapter 5
Next explain both the potential threat posed by viruses and other malicious codes and their main effects on computers and productivity.
. We are living in a digital era. This can include cyberstalking distributing pornography and trafficking. The virus spreads when an infected file is passed from system to system.
Various types of viruses. The most common examples of malicious code out there. The virus is the oldest Malware type and one of the most common.
Next explain both the potential threat posed by viruses and other malicious codes and their main effects on computers and productivityDiscuss the fundamental lessons that we can learn. Possibly the most common type of malware viruses attach their malicious code to clean code and wait for an unsuspecting user or an automated process to execute them. Malicious software malware infects devices without users realizing its there.
As its name suggests Spyware is a common type of malware designed to spy on target users and gather information such as credentials bank details internet activity transaction details and more. This type of virus infects the system by appending itself to the end of a file. This code can be used to steal important information like.
This is the least common cybercrime but. 7 Examples of Malicious Code. Among the ever-growing list here are some common culprits.
Malware short for malicious software is a blanket term for viruses worms trojans and other harmful computer programs hackers use to wreak destruction and gain access to. To see how viruses and other types of malicious code operate we examine four types of malicious code that affected many users worldwide. It changes the start of a program so that the control jumps to its code.
In doing so hackers gain access to private data stored on the network and can go as far as to steal leak encrypt or completely wipe it. Malware code includes two types of elements static and dynamic. A quick static analysis often reveals enough information needed to create an indicator of compromise IOC a document recording the softwares malicious nature.
Another class of malicious code is written for a particular system for a particular application and for a particular purpose. Identify at least three 3 different types of viruses and describe the main differences between each one. TARGETED MALICIOUS CODE.
Viruses can be harmless or they can modify or delete data. An email virus attaches itself to an email that is sent from one user to another. These malicious programs include spyware viruses trojan and ransomware.
Types of Malware. Many of the virus writers techniques apply but there are also some new ones. Malicious hackers can go about this in a variety of ways including the ones listed below.
Types of Cyber Attacks. The following is a list of some of the more common malware types and definitions. Explain the key differences between viruses and other malicious codes.
The types of malicious code are. Identify at least three different types of viruses and describe the main differences between each one. First Example of Malicious Code.
Malicious code may also include time bombs hardcoded cryptographic constants and credentials deliberate information and data leakage rootkits and anti-debugging techniques. Explain the key differences between viruses and other malicious codes. Up to 20 cash back Types of malicious code.
This category of cybercrime involves one individual distributing malicious or illegal information online. Malicious code describes a broad category of system security terms that includes attack scripts viruses worms Trojan horses backdoors and malicious active content. Now a day most of the people use computer and internet.
In general most experts view the term malware as a contraction of two words malicious software. Variations include Trojan horses spyware ransomware malvertising and viruses. So far we have looked at anonymous code written to affect users and machines indiscriminately.
The systems of your customers admins and other users might have Trojan Horses downloaded on them. After the execution of its code the control returns back to the main program. The Brain the Internet worm the Code Red worm and web bugs.
Many malicious code types can harm your computer by finding entry points that lead to your precious data. The Brain Virus. This is a malware that relies on someone or something else to propagate from one system to another.
It uses malicious code to alter computer code logic or data and lead to cybercrimes such as information and identity theft. Viruses A Virus is a malicious executable code attached to another executable file. Attackers inject malicious codes into trusted websites and applications and when a user visits such infected web page the malicious JavaScipt code is executed on the users browser.
It distributes its own copies to other non malicious programs by modifying them. This type of analysis focuses on the former examining static properties like metadata headers embedded assets etc. Its execution is not even noticed.
Malicious code is designed to grant cybercriminals unlawful remote access to the targeted system thus creating an application backdoor. There are numerous malware types however we have shortlisted some of the most common and dangerous types of malware attacks. For more details refer to this.
Viruses are self-replicating malicious code that attaches to macro-enabled programs to execute. Based on the infiltrating nature attack type and damage levels malware are broadly classified into 12 types. The different types of Computer virus are Memory-Resident Virus Program File Virus Boot Sector Virus Stealth Virus Macro Virus and Email Virus.
One of the earliest viruses is also one of the most intensively studied. Malware includes computer viruses worms Trojan horses ransomware spyware and other malicious programs. These targeted malicious code.
These programs can easily swipe any sensitive data that might be present on the infected systems and may also infect your website. It is a computer program that after infiltrating the system replicate itself by modifying the codes of other programs. A cyber-attack is an exploitation of computer systems and networks.

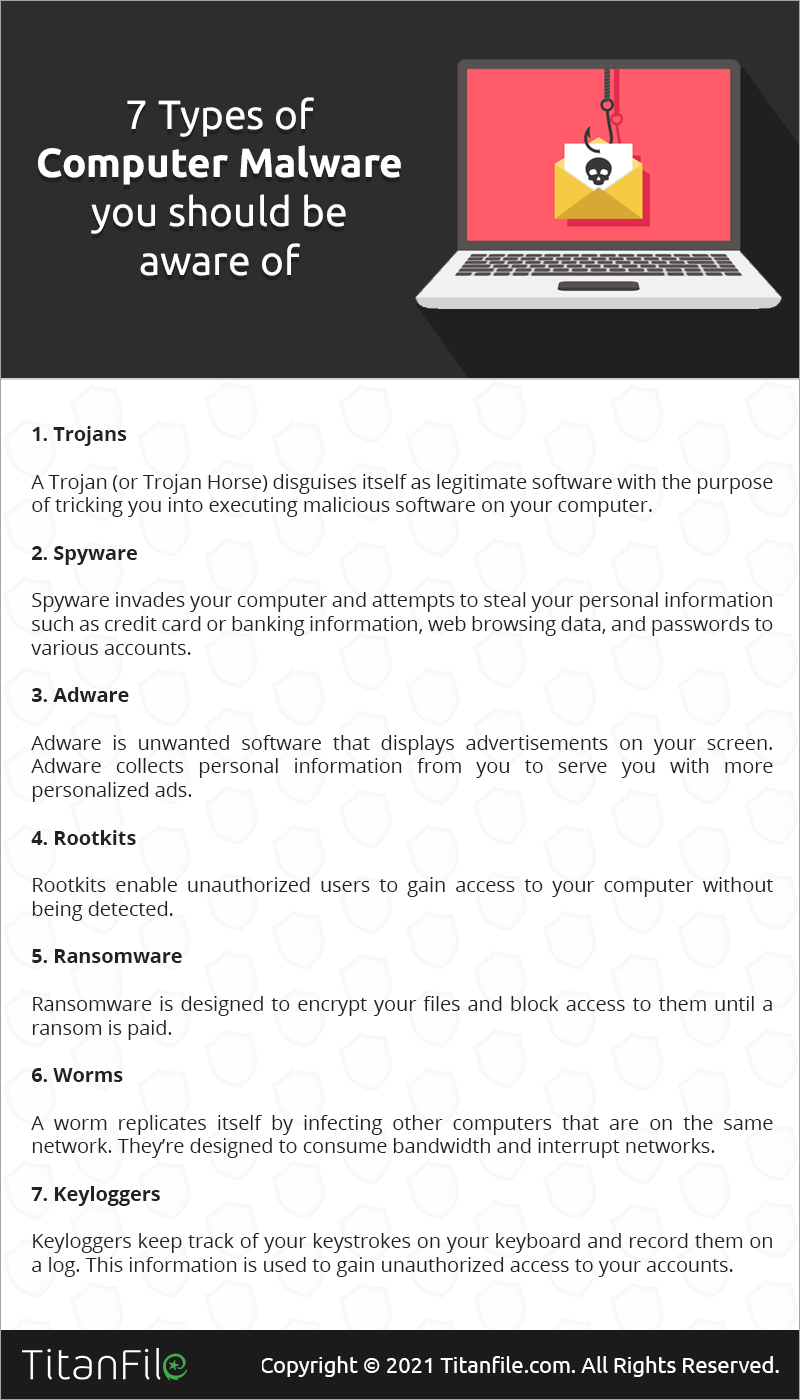
7 Types Of Computer Malware And How To Prevent Them In 2022 Titanfile

Virus And Malicious Code Chapter 5
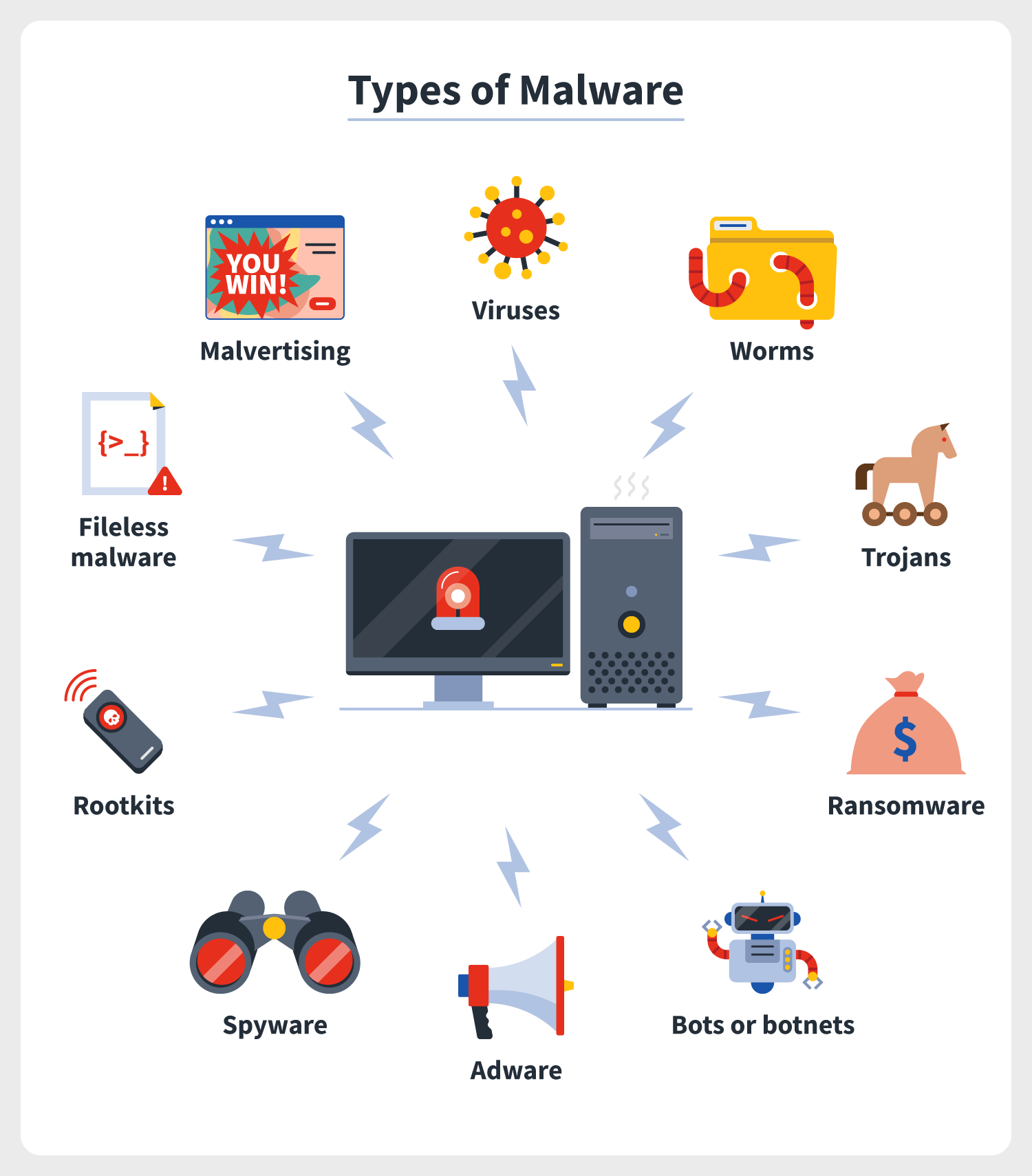
10 Types Of Malware How To Prevent Malware From The Start Norton
Comments
Post a Comment